Which Of The Following Best Describes A Honeypot
So, you've stumbled across this super weird phrase: "honeypot." Sounds kinda sweet, right? Like a sticky, golden pot of deliciousness. Well, it is, in a way! But not for you. Unless you're a super sneaky hacker, that is.
Basically, a honeypot is a digital trap. Think of it like leaving out a big, juicy steak for a hungry wolf. You know it's gonna attract attention. And guess what? That's exactly the point!
We're gonna dive into the fun, quirky world of cybersecurity. And this "honeypot" thing is seriously one of the coolest tricks up its sleeve.
Imagine your computer or network is like your super cozy home. You've got your valuables, your photos, your… well, whatever you keep on your computer! You want to keep it safe, right?
Hackers, on the other hand, are like those sneaky little critters who try to get into your home. They're looking for an easy way in. They want to poke around, maybe steal something, or just cause a bit of mischief.
A honeypot is like setting up a fake, tempting room in your house. This room looks super easy to break into. Maybe the window is slightly ajar, or the door handle wiggles a little too much.
But here's the kicker: this room is actually a digital decoy. It's not where your real treasures are kept. It’s designed to be found. It's designed to be attacked.
And why would anyone want to be attacked? That’s where the fun begins!
Think of it like this: Instead of guarding every single door and window of your house with a grumpy guard dog, you build a tiny, irresistible gingerbread house right in your yard. The gingerbread house is decorated with candy and looks like it's full of delicious secrets.
The wolf (the hacker) sees the gingerbread house. "Ooh, easy target!" it thinks, and happily trots over to investigate. Meanwhile, your actual house is locked up tighter than a drum.
So, what best describes a honeypot? Let's break it down.

Is it a sweet treat for hackers? Nope! That would be too easy for them.
Is it a security camera? Kind of, but it's more active than just watching. It's actively baiting.
Is it a warning sign? Not exactly. It's more of a lure.
The best way to think about it is as a deliberately vulnerable system. It looks weak. It looks like a prime target.
But in reality, it's a sophisticated setup. It's a carefully constructed piece of digital bait.
When a hacker attacks a honeypot, it’s like they're stepping into a digital pit. A pit that’s not designed to hurt them (usually!), but to observe them.
Think of it as a high-tech bug zapper. The bug (hacker) is drawn to the light (the vulnerable system), and zap! It's captured. But instead of getting zapped, the honeypot is recording everything.
It’s like having a secret spy agency. They create a fake, tempting target. Then, they watch with bated breath as the bad guys come sniffing around.
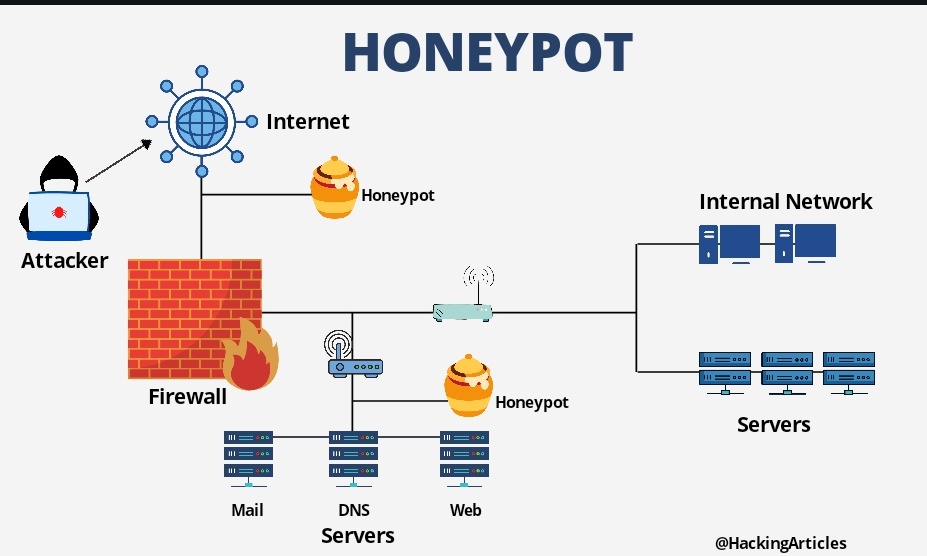
What do they learn? Oh, so much!
They learn how the attackers operate. What tools do they use? What are their techniques? What are they looking for?
It's like being a wildlife photographer. You set up a blind, you lure in the rare animal, and you get incredible footage of its natural behavior.
With a honeypot, cybersecurity experts get a front-row seat to the hacker's playbook.
This information is gold! It helps them understand new threats before they become widespread. It helps them build better defenses for real systems.
It’s a way to study the enemy without actually being in danger.
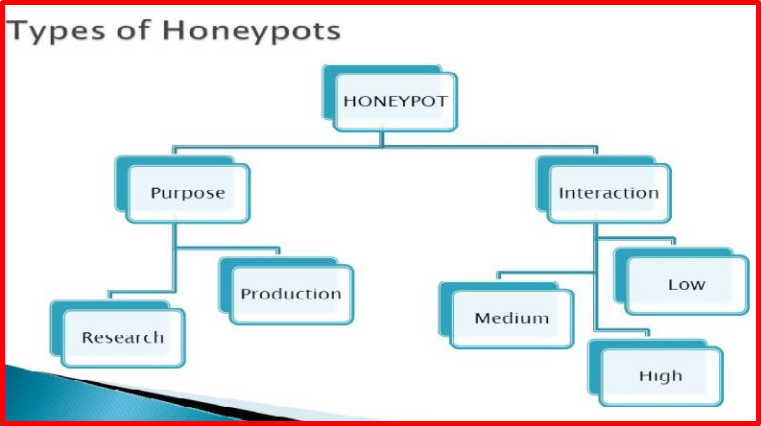
There are different kinds of honeypots, too. Some are super simple, like a single fake computer. Others are way more complex, mimicking entire networks!
Imagine setting up a fake online store. It looks totally legit, has all the bells and whistles. But it's just a trap. As soon as someone tries to "buy" something, alarms go off, and the system starts collecting data.

It’s a bit like those movie scenes where the hero sets a trap for the villain. The villain confidently walks into the trap, thinking they’re winning, and then… surprise!
One of the funniest things about honeypots is the sheer ingenuity involved. People spend a lot of time and brainpower designing these things to be just tempting enough.
It's a game of cat and mouse, but in the digital realm. And the honeypot is the super-clever mousehole that the cat can't resist investigating.
So, back to our question: Which of the following best describes a honeypot?
It's not a secret password. That's for protecting things.
It's not a firewall. That's for blocking bad stuff.
It's not a virus scanner. That's for finding bad stuff that might have already gotten in.
It's a decoysystem. A digital lure. A trap designed to attract and observe attackers.

It’s a system that is intentionally made insecure to attract cyberattacks.
Think of it as a controlled experiment. You're not just hoping hackers stay away; you're actively inviting them to show you their moves.
It’s a bit like setting up a fake treasure chest in a desert. You know pirates will be drawn to it. And when they get close, you can see exactly how they plan to crack it open. Then, you can go back and reinforce your real treasure.
It’s a proactive defense. Instead of waiting for an attack, you’re creating an opportunity to learn from one.
And the best part? It’s just plain fascinating. It’s a peek behind the curtain of the digital world, where cybersecurity professionals are constantly outsmarting the bad guys.
So, next time you hear the word "honeypot," don't think of honey. Think of a cleverly disguised trap, a digital decoy, and a whole lot of fun for the good guys.
It’s a system that’s meant to be breached, but only by the right people, at the right time, and for the right reasons. And those reasons are all about making our digital world a little bit safer, one sweet, sticky trap at a time.
It's a bit like a dare. "Come on, try and break into this! We're waiting to see what you've got." And when they do, they're not winning; they're just proving the honeypot works perfectly.
It's a smart strategy, a clever trick, and a seriously cool part of the cybersecurity world. Who knew being a little bit vulnerable could be so powerful?